What’s Single Sign-On and what’s so “singular” about it?
by Alexandre Dedourges, DevSec
Indeed, as part of your business activity, you may need to use different services. The latter often require employee authentication to operate. Thanks to SSO, this process is simplified through centralized authentication. SSO is designed to help companies better manage workforce authentication for the sake of security and improved user experience. This way, IT services are able to better handle password-related security rules: account setup, employee departure, amendment of a compromised password… With only one password to be memorized by each employee, SSO will considerably lessen the requests for password resets sent out to administrators.
Thus, SSO combines numerous advantages for companies and employees alike: security, simplicity, productivity… It also allows to better address cybersecurity challenges thanks to a centralized password management policy.
In a nutshell, SSO is “a password to connect them all” - guess which film we got it from 😉
A small hint:

SSO, a single password that allows for multiple authentications
SSO is an extremely convenient tool in an interconnected world. Indeed, it will allow you to greatly simplify the connections within your company. Are you having difficulties with authentication processes? Are you working with more and more SaaS? Are you a SaaS and wish to make your services available to as many people as possible? Then SSO is made for you.
First, here’s SSO’s main advantage: it allows you to dramatically reduce the number of passwords that your employees have to use as part of their activities. Single authentication, as its name suggests, will allow for the use of a single password for several services.
Let’s take the example of a sales company:
As part of its activity, a given company needs to access inventory management through a software, employee management through another, and many other services.
Without SSO, an employee will need several passwords to access all of these softwares and services. It can quickly become a pain to remember all of them.
With SSO, an employee will log in to their SSO (also called Identity Provider). This IP has a so-called ‘trust relationship’ with various services (also called Service Providers). This relationship will allow users to be identified and to access all the trusted services. In that case, they will then be able to access the inventory management software and/or HR management software, if given access by their company, via a single password.
Thus SSO solves the problem of handling too many passwords. In 2018, a study conducted by Dashlane (a password manager) and Virginia Tech revealed that an average user handled more than 150 accounts. In the year 2022, the figure might even go up to 300. That means just as many passwords to memorize. In order to maintain a healthy digital hygiene, it is necessary to use one password per service and to change it regularly. And yet, in practice, 34% of users (according to that same study) are only using one password for several platforms.
SSO, a single password yet numerous advantages
The single biggest advantage, as mentioned earlier, is the fact that it reduces the number of passwords. Using just one password implies a simplified and smoother user experience: no need to remember dozens of them. Besides, single authentication makes it easier to change passwords regularly. Indeed, it is simpler to modify just one password frequently rather than hundreds of them.
Lastly, using an SSO enables employees to focus on the strength of their password rather than the capacity to remember them. One way for them to do so is by using a “passphrase” or mnemonic word combination. Passphrases are the safest type of password to date. For instance, a complex password such as “LyQWZ.bu8cFdpS” is not as strong as a passphrase like “One SSO to connect them all!”. The longer the password, the harder it is to “crack” it.
Thus, SSO holds many advantages for your employees who will see their experience greatly improved. But single authentication also implies numerous benefits for the companies that adopt it!
SSO’s uniqueness also enables you to reduce the number of issues linked to forgetting your password. That it turns represents considerable time savings for companies, because there will be fewer procedures to follow in order to retrieve them. Besides, it means handling costs will be reduced. According to Gartner, taking all parameters into account (for example, the cost incurred by the time lost by both administrators and employees), password resets cost companies 60 euros on average. What’s more, they represent 20 to 50% of calls received by client support. Setting up an SSO therefore allows to reduce requests for password resets by 50%.
Moreover, by centralizing authentication, SSO will enable the simplification of security policy by facilitating their definition and setup. This centralization, in turn, diminishes vulnerability to breakdowns or security breaches. By focusing on the strength of their passwords, users will simultaneously reinforce the security of your company.
Nevertheless, SSO requires particular attention. As it gathers all services together under a single ID/password pair, it limits the likelihood of a risk yet increases the impact of a potential breach. That’s why it is crucial to set up a strong password policy - and, if possible, add one or several security layers to the authentication process.
A few solutions to better secure SSO
Multiple-factor authentication
First of all, the simplest way of increasing SSO security is using double or multiple-factor authentication methods. According to Microsoft, setting up this type of security device reduces risks by 99.9%. Some examples include:
- OTP Authentication (One Time Password)
Generally speaking, the user will need their cellphone to prove they are the ones trying to log in. For instance, they may receive a single-use code on their phone which they will then have to write down in the SSO. They may also use an app.
- TOTP Authentication (Time based OTP)
Similar to the previous solution, except the codes provided will only have a short lifetime for every new service.
- Biometric authentication
Biometric authentication allows for reinforced security as it uses parameters that are unique to every user (fingerprint, facial recognition…)
Le SCIM (System for Cross-domain Identity Management)
SCIM is a protocol that complements SSO perfectly. Indeed, as your company grows and expands, the number of employees increases accordingly. Therefore, the number of identities to be handled becomes bigger and bigger, and the work of IT teams gets more and more complex. Only setting up an SSO doesn’t allow you to ensure that identities will remain up-to-date on all services. When a new employee arrives or when someone changes their name, this means identities need to be handled, created or updated. Making these changes by hand would be a long and tedious job for your IT teams - especially in the context of rapid growth for your company.
That’s where SCIM comes in. SCIM is a protocol created in 2011. It allows you to stop worrying about updating identities. As a matter of fact, once you set it up with your SSO, each identity change on the identity provider’s side will be taken into account and spread out on all the services that use this SSO. Thus the security of your system will be preserved. For instance, an employee who left your company will no longer be able to access the services they used to log in to. Similarly, someone who changed their name after getting married will have their profile updated on all their services.
To sum up, SCIM enables you to keep data up-to-date to avoid any problems. As a matter of fact, such issues occur frequently, according to a study on employee access in companies conducted by Beyond Identity. The latter reveals that 83% of employees have already kept access to their former companies after leaving them. What’s more, 56% of them have tried to harm their former employers by using their previous login information. Lastly, 74% of employers claim to have been negatively impacted by an employee who has kept their access info. That’s why keeping identity information up-to-date is crucial for companies. This is known as identity lifecycle management.
Besides, according to the OWASP (Open Web Application Security Project), the problems stemming from access control inside companies were ranked #5 in 2017 and #1 in 2021. Hence reliable identity management is essential, and the use of SCIM is greatly recommended. If you wish to know more about SCIM, please don’t hesitate to see our article.
SSO: how does it work?
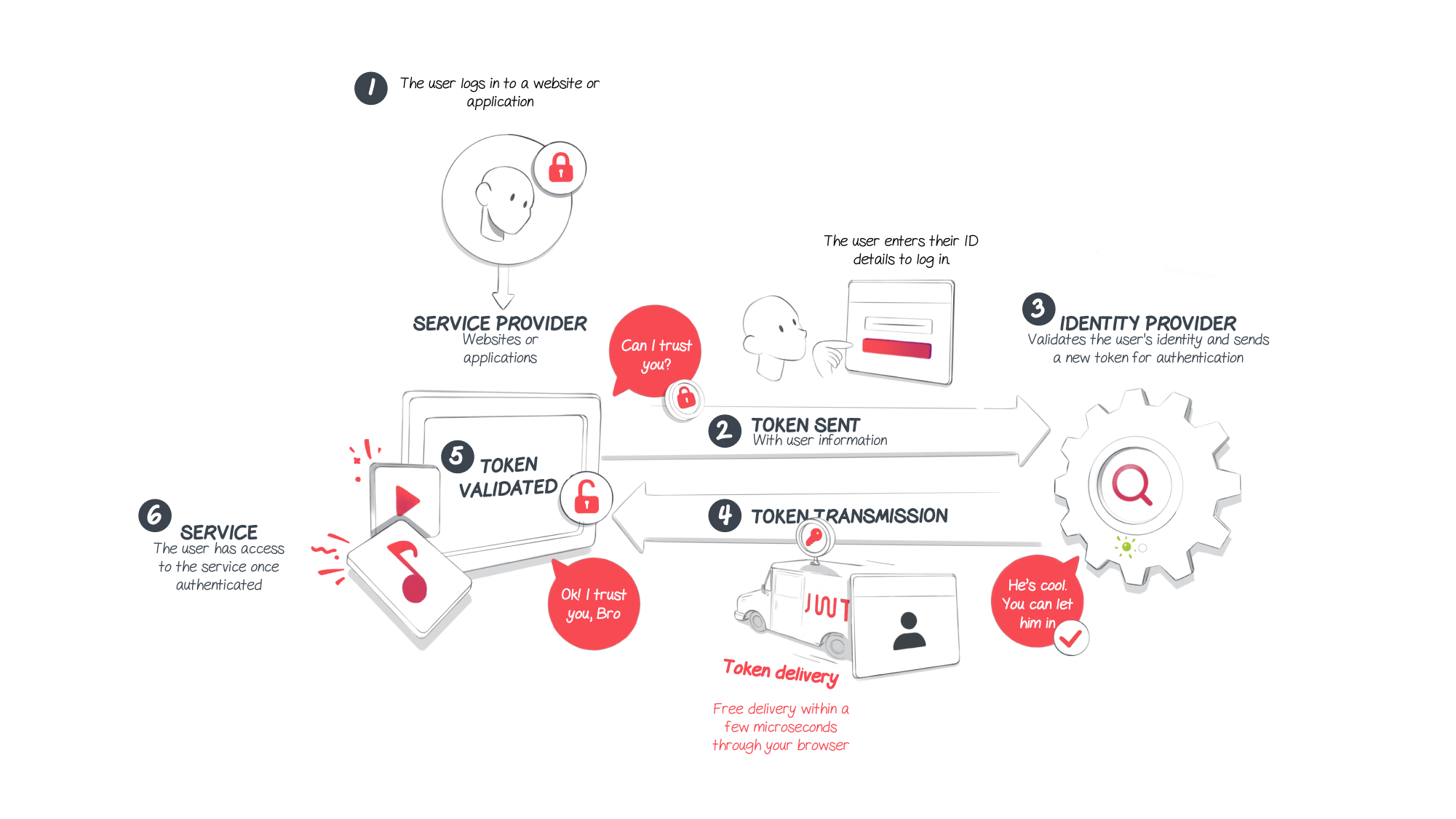
1.A user will log in to a website or an app (the service provider) required for their activity.
2.To log in, the user will enter their ID details just like on any website or app. The service provider will then generate a token based on the information provided by the user. This token will then be sent to the SSO (the identity provider).
3.If the details provided by the user are correct, the identity provider will validate them. Then, it will send a new token to the service provider in order to validate authentication.
4.The transport of this token from the identity provider to the service provider takes place through the user’s browser.
5.This token is then validated by the service provider, who is tied to the identity provider through a trust-based relationship.
6.Once the whole process is completed, the user is given access to the service.
SSO VS Social Login
Single authentication might seem familiar. When browsing the Internet, one quickly realizes that a lot of websites offer the possibility of authenticating via other widely used platforms (Facebook, Apple, Google…). That’s why this method might resemble that of SSO. If the way this authentication method operates is indeed virtually similar to SSO, in practice, it’s actually called Social Login. It enables users to log in to services they use in everyday life (online shopping, social networks…). SSO differs in that it’s used mainly for the sake of authentication within companies. Thus, rather than signing on through a platform such as Facebook, your employees will log in to the services your company uses via their company identifier. You will then have the possibility to manage password policy as well as security rules.
In an increasingly connected world, SSOs are becoming more and more important
An increasing number of companies are requiring SAAS (Software as a service) to use their SSO system for a safer and smoother authentication process by their employees, as well as for compliance issues. Therefore, one of the objectives for SAAS is to become “SSO ready”, i.e. to be able to connect to the various types of SSO and identity providers that they may encounter through their clients or prospects. Consequently, meeting this requirement is both a matter of security and business when it comes to growing your market and contracting with clients who have such expectations. With just a few lines of code, Cryptr can make your authentication compatible with all types of SSOs (SAML, ADFS, OIDC) and identity providers (Okta, Ping Identity, Auth0, OneLogin, Google,...) that you might encounter through clients or prospects.
So… are you prepared to become “SSO ready”? Find out more on Cryptr!
And to chat with our teams, you can book the slot of your choice by clicking here: Meet Cryptr
Add enterprise SSO for free
Cryptr simplifies user management for your business: quick setup, guaranteed security, and multiple free features. With robust authentication and easy, fast configuration, we meet businesses' security needs hassle-free.