What’s the point of Active Directory?
by Alexandre Dedourges, DevSec
In computing, a directory represents a data storage system. The Lightweight Directory Access Protocol is a protocol through which one can handle these directories. Thus, the AD (Active Directory) will allow to use and edit directories. Companies largely use directories to manage identities and computer parks. Indeed, they make user and device management easier by centralizing them.
Data management through directory service
Directories derive from hierarchized databases, although they’re used differently. While a directory is mainly meant to be browsed rather than edited, this is not necessarily the case of a standard database. Unlike so-called “relational” databases, directories are structured on a hierarchical basis and not in tabular form. Their main specificity is that they allow the storage of data that lasts over time. Indeed, they are mainly used to store data that is rarely updated. For instance, one could find someone’s contact details, email addresses… Directories come in handy when looking for a very specific piece of data, as you can search according to particular criteria. The data that is found this way can then be used on other softwares.
Queries and changes based on the Lightweight Directory Access Protocol
The Lightweight Directory Access Protocol is the protocol used to query and modify directory services. It relies on the TCP/IP (Transmission Control Protocol and Internet Protocol). As a result of its growing usage, it has evolved to become a standard for directory systems. It is based on a tree structure, within which each node corresponds to an attribute associated to a value (key / value system). Other models exist, such as the X.500 by ITU (International Telecommunication Union) but the latter is more complex than LDAP.
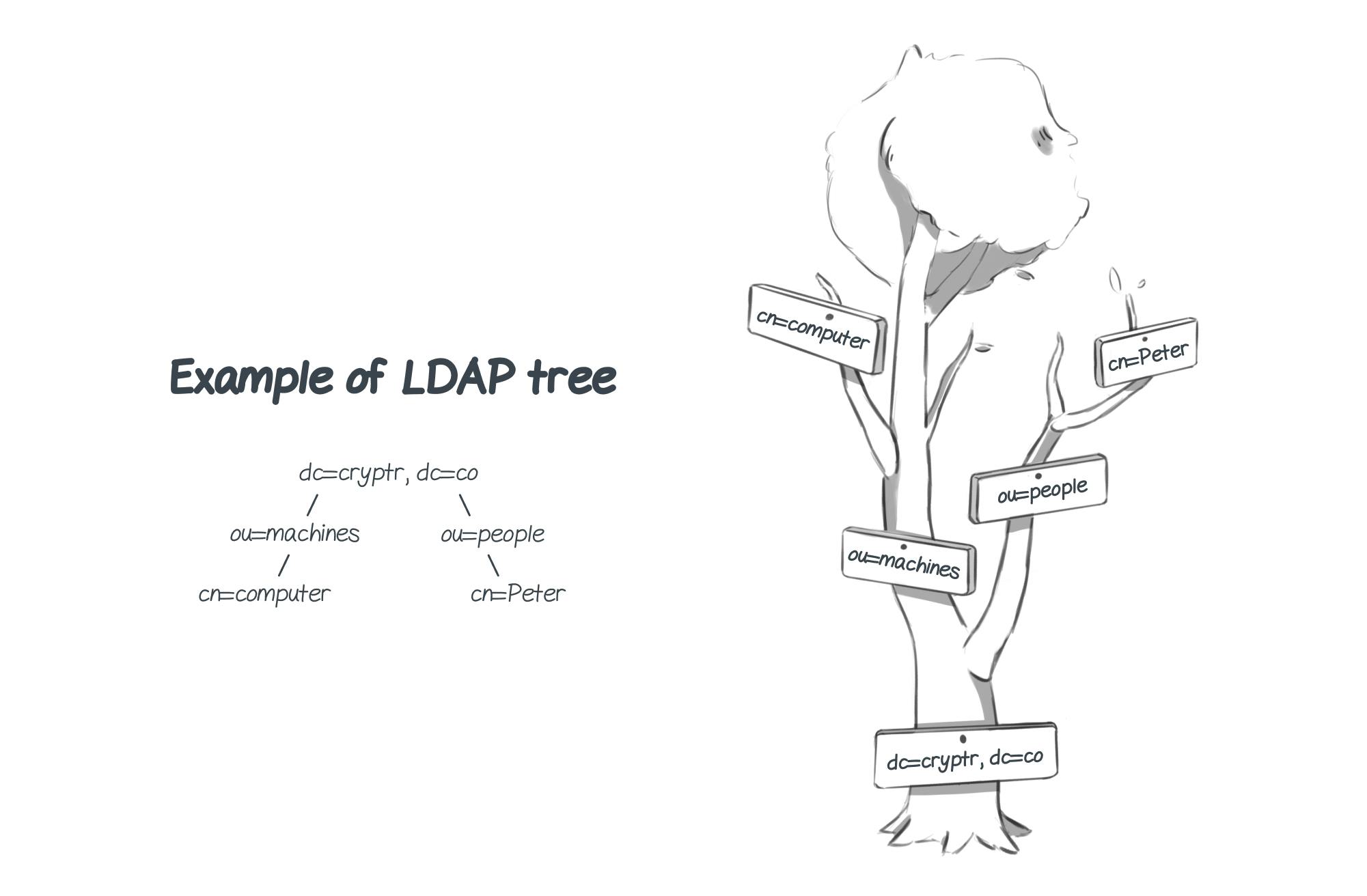
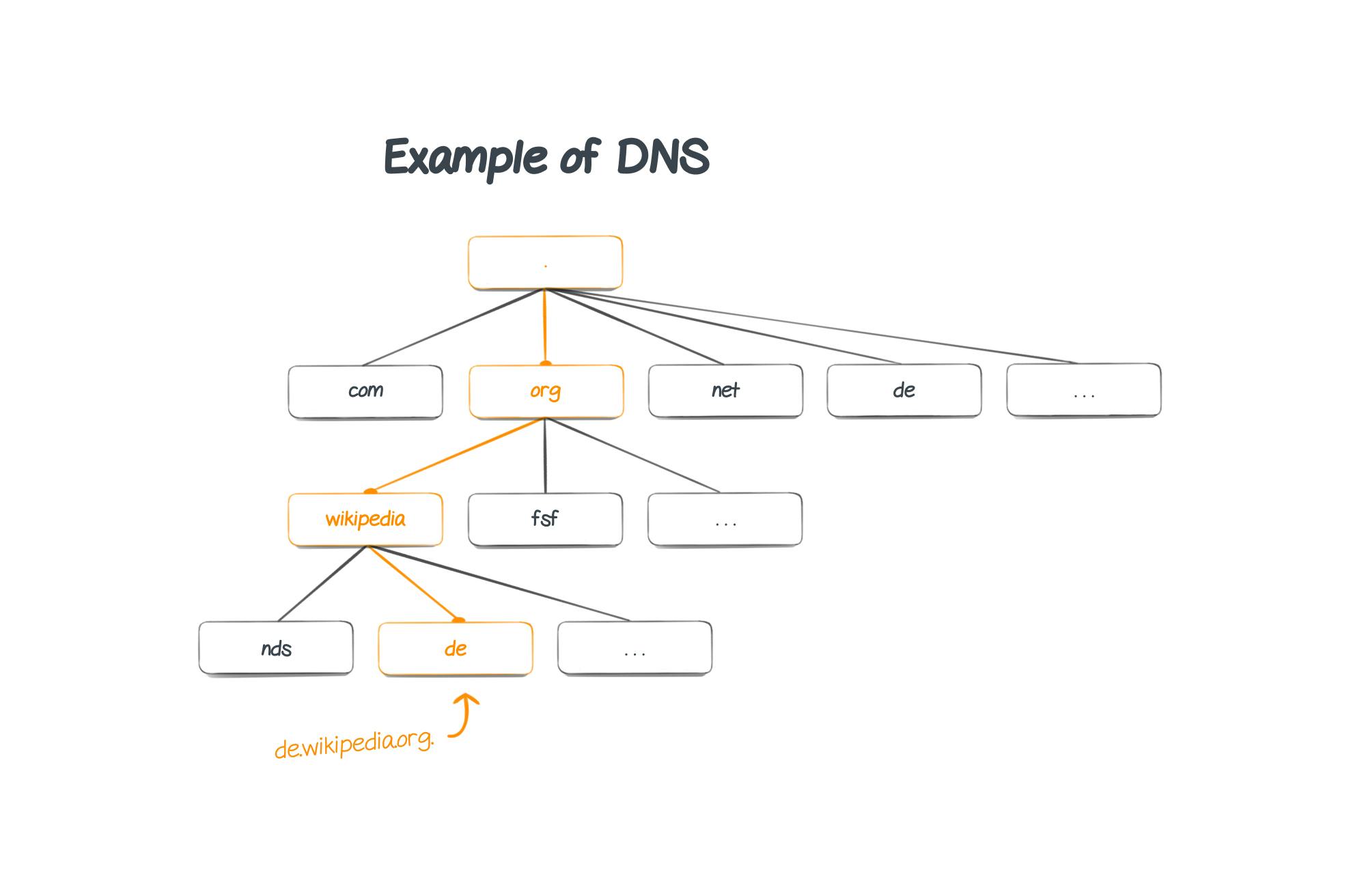
The current trend is to use the same naming as DNS (Domain Name System) for the directory’s base (root and first branches).
The components of LDAP structure are the following:
-
Domain Components (DC) for base objects
-
Organizational Units (OU) for further branches, representing organization groups or units
-
Common Name (CN) for unique objects or people
-
Identifiers (UID) for unique objects or people identifiers
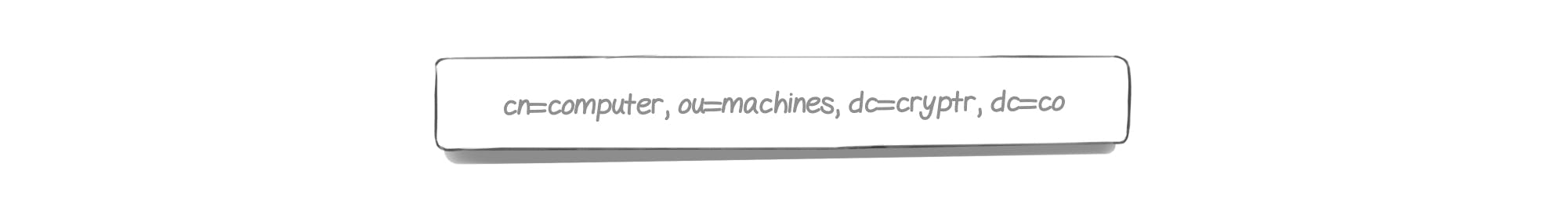
Finally, the Distinguished Name represents the combination of all elements within a given branch. If we take our last example:
The current LDAP version is version 3 (LDAPv3), which is defined by IETF (Internet Engineering Task Force) in several of its RFCs (Request For Comments). These RFCs are specification documents which are one of the foundation stones of the Internet.
Active Directory for identity management within companies.
Active Directory’s main objective is to set up centralized services for authentication and identification purposes on a computer network. It may be used with all kinds of systems, whether it be Windows, MacOS or Linux. On top of these services, the Active Directory also allows to manage the attribution and application of group strategies (which in turn allow the management of computers and users within an Active Directory environment.)
The AD will help index all elements of a network. It will be possible to include user accounts, servers, workstations, shared folders, connected devices (e.g. printers)... This way, one will be able to define rules and rights for each element belonging to the AD. Thus, a user will easily be able to retrieve a shared resource. As for administrators, they’ll be in a position to control resource usage through various features.
For instance, let’s take a company with 1000 employees. Each piece of employee information will be indexed in the directory (name, first name, position, password…) as well as their rights. This way, a protected file or a sensitive computer will only be accessible by an employee with appropriate access rights. Once authentified, the user will be able to access the requested resource on the condition that they have the necessary authorization.
Therefore, Active Directory constitutes a sizable advantage for managing identities and access rights within companies - especially when they start to grow.
Simplified park management
Active Directory is also a good tool for managing computer parks. Indeed, if properly set up, it will tell you in which service a device is located, for example.
In order to use it on other systems than Windows’ (Windows Server), it is necessary to go through Samba, an interoperability software. It implements Microsoft Windows’ proprietary SMB protocol (Server Message Block) / CIFS (Common Internet File System). It can be used on computers running the Unix operating system and its by-products.
Active Directory and domain controllers
In order to operate, Active Directory needs a main service - i.e. Active Directory Domain Services. AD DS is part of the Windows Server operating system. Each server operating AD DS is called a domain controller. Most of the time, companies have several domain controllers. Each of these can keep a copy of the entire domain’s directory.
In order to keep information up-to-date, each domain has the possibility to communicate its data to others whenever a change occurs. Thus, domains are able to preserve the entirety and consistency of their data. When several directories are used, a global catalog is necessary. The latter is a central directory built automatically on the basis of a partial copy of information stemming from the different directories of the network.
AD and ADFS (Active Directory Federation Services)
Active Directory Federation Services is a component of Windows Server. It can be installed on Windows servers. It facilitates users’ access to applications and systems. Indeed, it allows to perform authentications outside of the forest. It is particularly useful in an increasingly connected world, where one often has to connect to third-party applications that are not handled by AD. All in all, AD is extremely handy as long as its use remains within the forest. As for ADFS, it is a way to solve this problem by implementing authentications outside of it.
A few important terms in Active Directory structure
There are three different so-called “functional” levels within the Active Directory, i.e. domains, trees and forest.
Domain: A group that connects users, computers and other unique objects. It can be defined as a management area.
Tree: A collection of several domains
Forest: A set of trees. It can be defined as a security boundary. In order to interact, objects from different forests need their respective forests to have established trust-based relationships between one another. This does not apply to domains. Indeed, within a given domain, objects can interact even if they don’t belong to the same domain.
Active Directory in the Cloud with Azure AD
AD’s main defect is that it cannot be used in the Cloud, but only within on-site environments. In order to use it with Cloud ecosystems, one can use Azure Active Directory. Although two different elements, these can be used simultaneously - in the case of a hybrid setup where a company has one environment in the Cloud and another one on the website.
Active Directory, a tool used massively by big companies.
Active Directory is a very useful tool when it comes to handling identities, access rights, authorizations as well as managing computer parks. Today, it is used massively in big companies - so much so that almost 90% of Global Fortune 1000 companies use it as their main authentication and authorization tool, according to Frost.com. Microsoft Active Directory, though in decline, remains a widely used solution. Are your clients using AS? You can use our solution to set up an ADFS.
So, are you ready to learn more about AD? Find out more on Cryptr.
Add enterprise SSO for free
Cryptr simplifies user management for your business: quick setup, guaranteed security, and multiple free features. With robust authentication and easy, fast configuration, we meet businesses' security needs hassle-free.