What is a DDoS Attack (Distributed Denial-of-Service)?
by Alexandre Dedourges, DevSec
What is a DDoS attack?
Nowadays, more and more companies, SaaS or even individuals rely on the Internet. If a bank, an e-commerce platform or a SaaS is cut off from the Internet, it can be disastrous for their business. Some ill-intentioned competitors might want to make this happen as they greatly benefit from doing so. One of the most common methods to do this is the DDoS attack. Indeed, this type of attack will consist in blocking your access to the network and the Internet. Thus, all or part of your activity will be paralyzed. This can have both financial consequences or on your image. The strength of DDoS attacks is that they are easy to set up by the attackers. Moreover, they can be particularly effective on targets with little or no preparation.
It will therefore be very important for a company or a SaaS, to be well prepared for this type of attack.
DDoS attacks, simple but powerful attacks that can have serious consequences.
DDoS (Distributed Denial of Service) attacks are attacks that make one or more services of a company unavailable. Like all attacks, they are intended to harm your business. There are several ways to cause a denial of service. For example, by exploiting a hardware or software vulnerability, but very often these are carried out by saturating the bandwidth of a network. Indeed, like any hardware, computer hardware has limits that DDoS attacks seek to reach in order to cause a shutdown or a malfunction of the hardware. Many hardware can be targeted (saturation of a router, a switch, a server, a database...). But they all have the same goal: to interrupt the normal operation of the service. If you are poorly protected, DDoS attacks could block your services for hours, and even days. This would have serious financial consequences or even on your image. All structures can then be concerned.
Who can be a target?
The targets of these attacks are numerous and varied. They can affect individuals, small structures and large companies. Nevertheless, they can only be used on entities whose activity depends on a network infrastructure communicating with the Internet. Therefore, a private individual with a router (an Internet box) can become a target. But in most cases, these attacks target companies, SaaS, governments, banks or data hosts. Indeed, the attackers often aim to paralyze your activity in a perspective of unfair competition, revenge or even ideology. A competing company would have every interest in seeing your activity cease or your image degraded. A former employee could want to take revenge by sinking your company. Finally, a hacktivist could want to protest against your decisions with an ideological goal. So there are many potential targets and attackers. DDoS being a type of attack relatively easy to set up, it is then necessary to protect yourself from it whether you are a big structure or a more modest one. Moreover, it is possible that you are a target of the attack, but also that you become the attacker yourself!
Indeed, if your machines are infected by a hacker in order to make them zombie machines, then he could use your machines to attack a target without your knowledge. However, the major problem is that you may have to stop your activity, following a cut of your Web services.
How can DDoS cut off your Internet services?
There are many ways to launch denial of service attacks. However, some are more common and used than others.
Use of botnets
To perform an attack on your services, an attacker can use botnets. Botnets are a group of compromised machines forming a network. This group of machines will send numerous packets (when sending a file, it is divided into several packets that will be sent one by one) to a target, which will saturate its traffic. This will cause a malfunction (difficulty or interruption of access to the Web). Numerous online services have been created that allow the use of botnets. These are often called "booters" or "stressers" and can be used by anyone. Although they are often paid for, some of these services can be used for free for a certain period of time. This is why DDoS is an extremely common and easy type of attack to set up. An ill-intentioned person could indeed use this type of service without having any computer knowledge.
Use of reflection
Reflection consists in usurping the IP address of a victim. An attacker will send packets to machines that are accessible from the Internet. By spoofing the victim's IP address, they are made to believe that it is the target of the attack that is the origin of its packets. The other machines will then respond by sending packets to this target machine. By repeating this on many machines in a repetitive manner, the victim machine will receive hundreds, even thousands of unsolicited responses. This can lead to a network overload and malfunction.
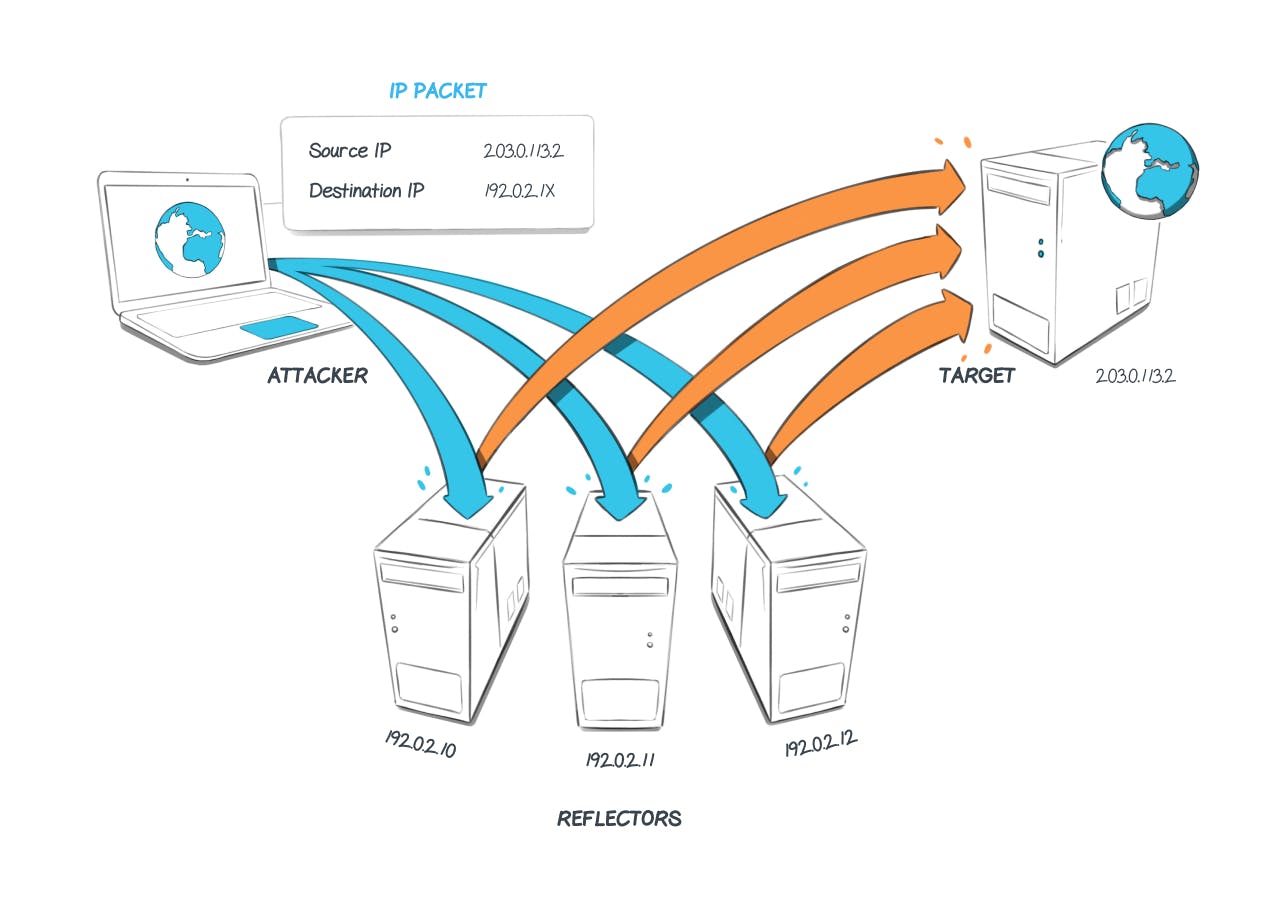
Use of amplification
Amplification consists of sending many packets to a target using protocols that generate very large responses compared to the basic request. By repeatedly sending very large responses to a service, the service will quickly see its allocated bandwidth saturated. This is called a volumetric attack. This works like a bottleneck.
Attack on applications
By sending numerous GET and/or POST requests to a service, an attacker could exhaust the processing capabilities of an application and thus alter its operation.
DDoS in a few numbers.
To understand the importance of DDoS attacks in our society, some figures can be helpful.
A growing number of attacks every year and a record in the beginning of 2022.
This beginning of the year 2022 has been marked by the beginning of the war in Ukraine. This war takes place both on the ground and in cyberspace. Since then, the number of cyber attacks have exploded. In fact, according to Kaspersky, The number of DDoS attacks in Q3 2021 increased by a factor of 3 compared to Q4 2020. The number of attacks in Q4 2021 increased by 1.5 times compared to Q3 2021 and finally the number of attacks increased by 1.5 times again between Q4 2021 and Q1 2022.
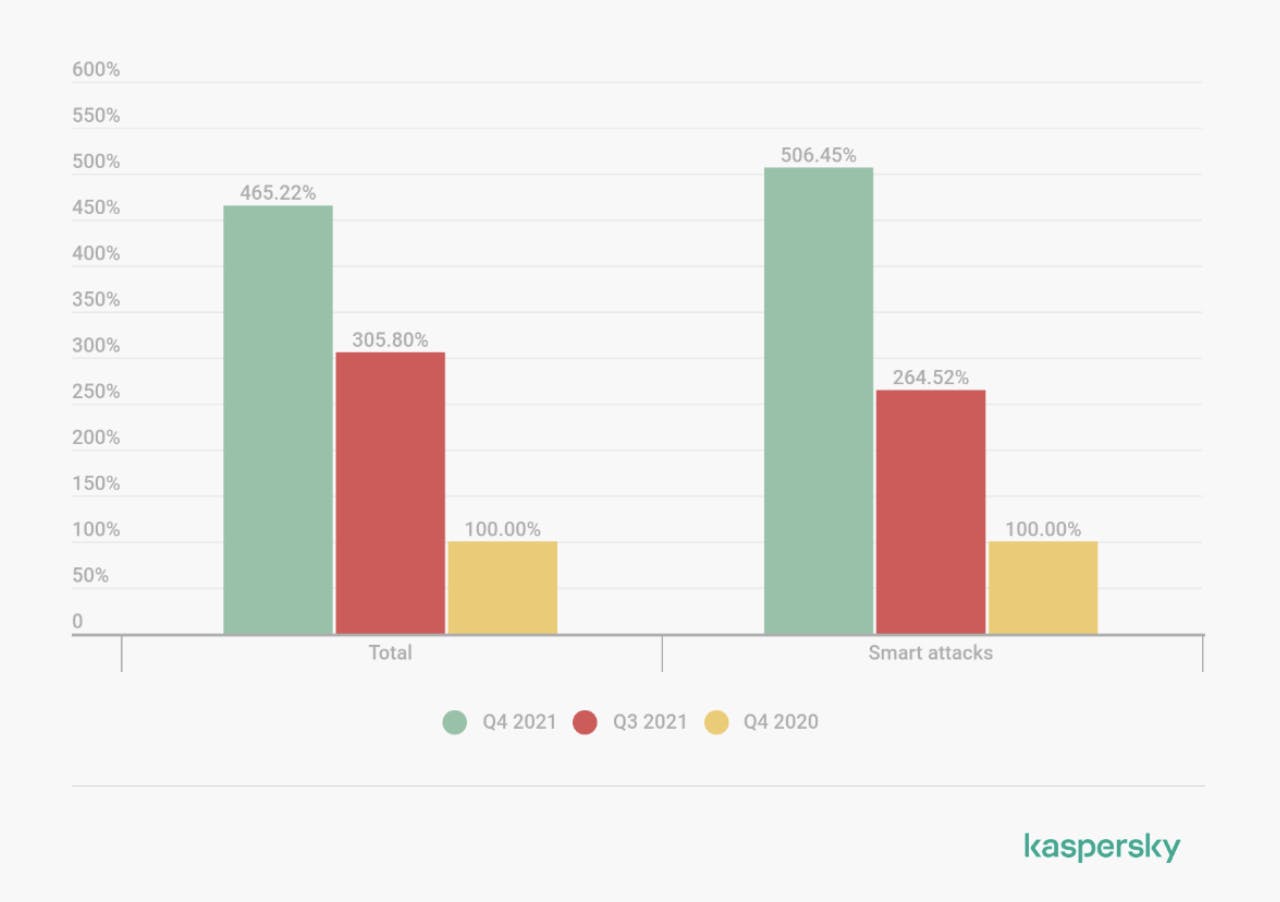
Comparative graphs of the number of DDoS attacks in Q4 2020, Q3 2021 and Q4 2021 (Source : Kaspersky)
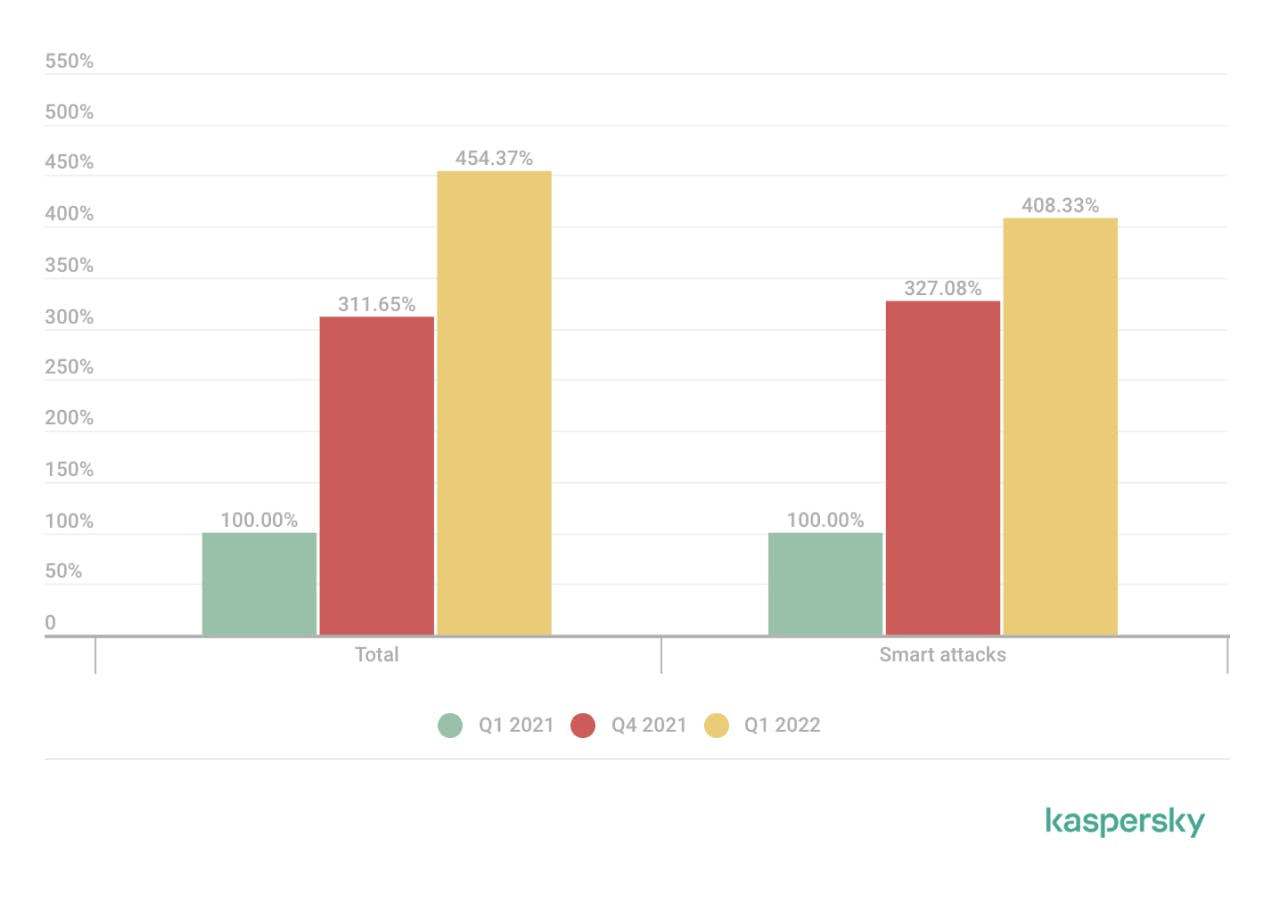
Comparison charts of the number of DDoS attacks in Q1 2021, Q4 2021 and Q1 2022 (Source : Kaspersky)
As a result, there are more and more attacks every year. Companies are still not sufficiently protected against this type of threat, which means that they are still widespread.
More and more massive attacks
The first documented attack dates back to the year 2000. The year in which a 15-year-old hacker named "mafiaboy" carried out a DoS attack on large Web and e-commerce services such as Amazon and eBay. These attacks would have cost these companies a total of about $1.7 billion, according to the FBI.
In 2018, the online service GitHub, widely used by developers to manage their application code was attacked. The attack was at the time one of the largest verifiable DDoS attacks ever recorded. The throughput of the attack reached 1.3 Tb/s, which corresponds to 1300 Gb/s. Source : Cloudflare
In February 2020, this figure was beaten, as AWS (Amazon Web Service) announced that it had mitigated an attack that reached 2.3 Tb/s of incoming traffic. Source : Cloudflare.
Finally, Microsoft announced that it mitigated an attack in November 2021 that reached 3.47 Tb/s. This makes it the largest DDoS attack in history to date. The attack targeted Azure customers in Asia. According to Microsoft, it originated from approximately 10,000 machines from several different countries (United States, China, South Korea, Russia, Thailand, India, Vietnam, Iran, Indonesia and Taiwan)...
Increasingly long attacks
Exacerbated by the war in Ukraine, DDoS attacks are not only becoming more frequent, but also longer. In fact, according to Kaspersky, the duration of DDoS attacks has increased significantly over the past two years. From Q1 to Q4 2021, the average duration of DDoS attacks was multiplied by 2.4. Then from Q4 2021 to Q1 2022, the average duration skyrocketed as a result of the war in Ukraine and increased by a factor of 80! The longest attack recorded at the beginning of the year lasted 549 hours, or about 23 days.
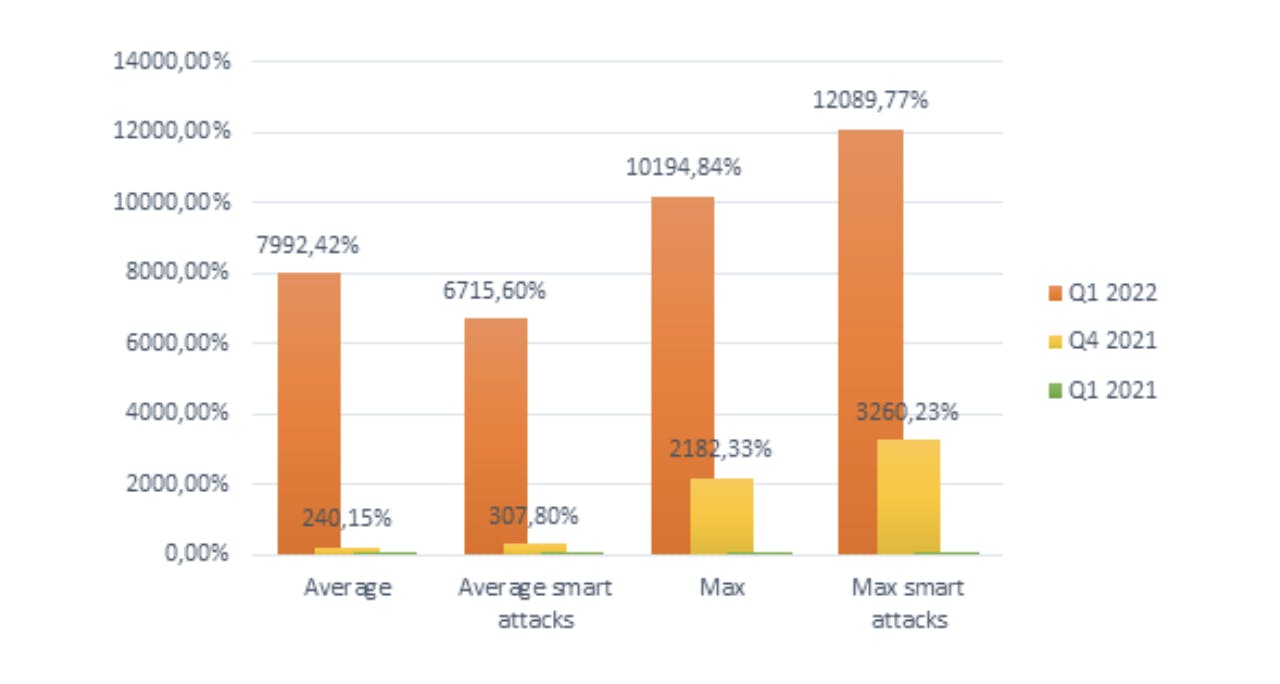
Graph of the increase in average DDoS attack durations in Q1 2022, Q4 2021 and Q1 2021 (Q1 2021 value is set to 100%) by Kaspersky.
Protect yourself against denial of service.
To protect yourself against this type of attack, there are several solutions and best practices to implement. First of all, it is necessary to monitor the network and the services operated. With the help of a SOC (Security Operations Center) for example. This monitoring will make it possible to follow the use of the various resources such as bandwidth. This will allow you to react immediately to the slightest suspicious sign. It is possible to supervise network traffic using NetFlow (network monitoring architecture developed by Cisco Systems) or IPFIX (IP Flow Information EXport) whose specifications are given in RFC (Request For Comments) 7011 of the IETF (Internet Engineering Task Force).
Once monitoring is in place, it is possible to implement protection solutions. Some solutions can be integrated directly at the transit operator (or ISP) level, which will be able to filter the incoming transit of the network.
The use of a CDN (Content Delivery Network) is also a source of additional protection. Indeed, a CDN allows a "caching" of the information of a website on several servers located in different geographical areas. When a user wishes to access the content of a website, the CDN closest to him will be used. This way, the answer will reach the user faster. This is a particularly convenient system for managing media streams. In addition to its increased speed, the CDN offers better availability and better protection against DDoS. By being distributed across multiple servers, the website can handle the load better. Although it is not intended to be a basic anti-DDoS solution, the CDN offers a significant advantage.
Finally, there are services dedicated to DDoS protection, for example via DNS redirection. It allows redirecting traffic to an external domain that will take care of filtering the traffic before redirecting it to its original destination.
This type of service is offered by Cloudflare, Arbor DDoS (NetScout), Incapsula (Imperva) or Akamai. Cloudflare was originally a CDN that has now evolved to offer many services to mitigate DDoS attacks.
You have probably already seen this web page. It is in fact a DDoS protection provided by Cloudflare that protects the site you want to access.
Akamai is one of the oldest CDNs on the market. It is also considered to be the biggest player on the market with servers almost everywhere in the world.
These two giants are both American, if you want to turn to a European alternative there is OVH CDN.
Finally, in some cases, organizations must declare DDoS attacks to the authorities. The OIV (Operator of Vital Importance) which are all the organizations considered as vital for the functioning of the country (Hospitals, transport...)
DoS VS DDoS
DDoS is actually a sub-category of DoS (Denial of Service), in fact, DDoS is a derivative of DoS, but more dangerous. DoS uses only one machine to attempt to overload the victim's network, while DDoS uses dozens, hundreds or even thousands. Even if one IP/machine is neutralized, there are still thousands of potential machines to protect against. On top of that, it is much more complicated to find the original attacker when thousands of "zombie" machines attack the target. This makes it an ideal attack for a hacker.
Protecting yourself against DDoS, a major issue for all companies and SaaS.
As we have seen, it is therefore very important for a company or a SaaS to be protected against DDoS attacks. The number of these attacks is increasing every year, and they are very simple to implement. This makes the probability of a DDoS attack on a service quite high, whether you are a small structure or a larger one. Moreover, an attack on a structure on which you depend could indirectly affect your own services. Hence the need to protect yourself at all levels. This can be done effectively by setting up network monitoring or using services like Cloudflare. Other types of attacks are of course likely to occur, but DDoS is a big part of the cyber threat landscape. If you want to learn more about how to protect your systems from DDoS you can visit the ANSSI (Agence Nationale de la Sécurité des Systèmes d'Information) website. The ANSSI offers a series of recommendations to protect your infrastructure and it may be worthwhile to implement them. We recommend reading their IT hygiene guide first. According to the ANSSI, these are the simplest and most basic rules, because they are the transposition of basic health security rules in the digital world. Therefore, all companies with a computerized service should adopt this hygiene guide.
At Cryptr, everything is done to work in a healthy digital environment and as secure as possible. DDoS protections are in place to ensure you have the best possible availability. So ready to learn more? Visit us at Cryptr.co !
Add enterprise SSO for free
Cryptr simplifies user management for your business: quick setup, guaranteed security, and multiple free features. With robust authentication and easy, fast configuration, we meet businesses' security needs hassle-free.