Understanding the difference between SOC2 & ISO 27001
by Alexandre Dedourges, DevSec
Security in IT is very important. When you have data to process or even simply IT services, it is essential to secure them. Of course, some services are more exposed than others (large groups, banks, governments...). If some companies can be satisfied with good IT practices, some require a higher level of security. Indeed, it is not uncommon for some SaaS to have to comply with high security requirements in order to work with large groups. Similarly, some companies need to have a certain level of security in order to work with states, for example. Security also has a strong impact on the image of companies that can expand their market and gain prospects by having a secure and reassuring infrastructure for their customers. It is in this context that ISO 27001 and SOC 2 the security standards have become world-renowned references.
ISO 27001 and SOC 2: two standards for better cyber security
ISO 27001
ISO 27001 or ISO/IEC 27001 is an international standard for information systems (IS) security. It was proposed by the ISO (International Organization for Standardization) and the IEC (International Electrotechnical Commission) in October 2005. It has since been revised in 2013 and published as "Information technology - Security techniques - Information security management systems - Requirements."
It is derived from the ISO/IEC 27000 suite of information security standards. These standards are recognized worldwide, the 27001 standard being the best known of them.
ISO 27001 defines the requirements for the implementation of an ISMS (Information Security Management System).
SOC 2
The SOC 2 is a type of security report. It was proposed by the AICPA (American Institute of Certified Public Accountants). The SOC 2 is also the result of a suite. The SOC is indeed a suite of 3 reports (SOC 1, SOC 2 & SOC 3) that can be written during an audit.
In addition, the AICPA's SSAE 18 (Statement on Standards for Attestation Engagements no. 18) defines two types of levels for its reports, Type 1 and Type 2. Type 1 includes an evaluation of the design of internal control, while Type 2 is more comprehensive and includes an additional evaluation of the operating effectiveness of controls.
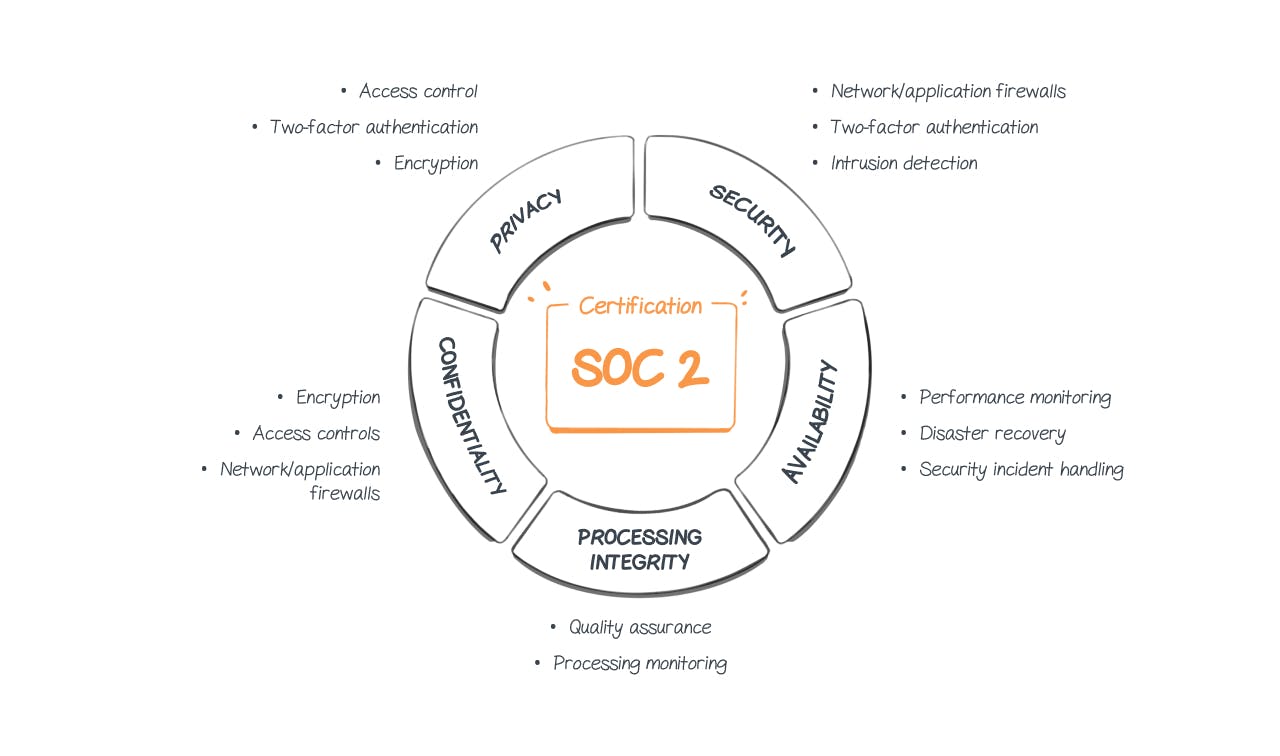
The primary purpose of SOC 2 is to define criteria for handling customer data. This is based on five criteria. These are called TSC (Trust Service Criteria) and correspond to security, availability, integrity, confidentiality and finally privacy.
Source: Impreva.com
The information security management system (ISMS)
The ISMS is a system defined in the ISO 27001 standard. It is even its main objective. Once implemented, it will ensure the security of the information.
Information security
Information security is defined by the 4 main principles of DICT (Availability, Integrity, Confidentiality, Traceability)
- Availability
Availability is the ability to perform a given function in the time allotted and under normal operating conditions. Here, accessing information in a normal and fast way.
- Integrity
The integrity of the information corresponds to the fact of preserving, treating or transmitting the data without these being altered or removed and this in an intentional or accidental way.
- Confidentiality
Confidentiality describes a behavior aimed at protecting data during its storage or transmission. This means that it cannot be intercepted or read by an unauthorized person.
- Traceability
The traceability allows us to follow the evolution of a data or a file, for example. It must be possible to know where it comes from, who made a modification, when, how...
To ensure these 4 main principles, ISO 27001 will rely on the Deming Wheel, also called PDCA.
The Deming Wheel or PDCA for continuous improvement.
The Deming Wheel is a method of continuous improvement. It is a method that consists in repeating several actions in an iterative way. Like TDD (Test-Driven Development) which is used to test and improve your applications.
Each letter of the PDCA corresponds to 1 phase. The four phases of the PDCA improve the functioning of a process in a continuous way. In the case of ISO 27001, it will improve the security of information and to ensure that it is always effective.
These 4 phases are: Plan, Do, Check, Act, hence the acronym PDCA.
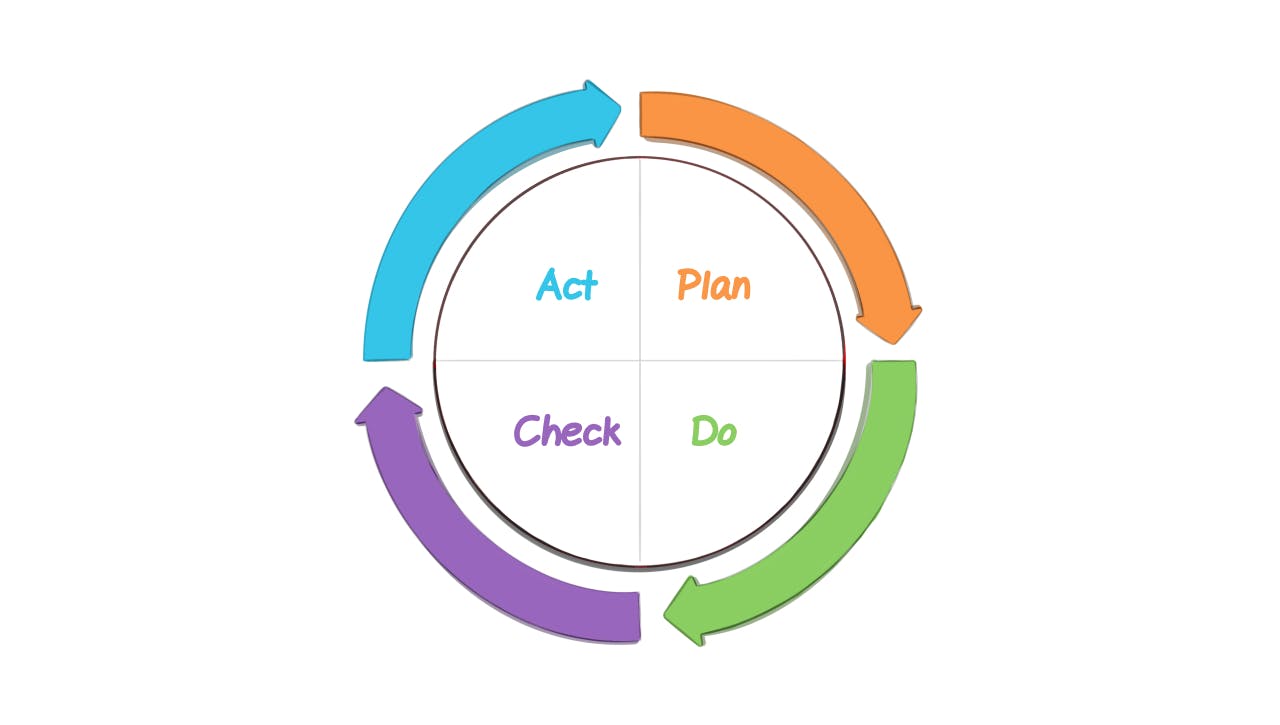
Plan
In this section, the goal is to plan what needs to be done to lay the foundation for ISM (Information security management). You will need to
-
Define the scope of the ISM (Information security management) and the security policies to be implemented.
-
Measure the risks (Probability / Impact), which can be done using a risk matrix.
-
Measure the previously established risk treatment
-
Define solutions that will mitigate these risks
It is possible to use methods such as EBIOS RM (Expression des Besoins et Identification des Objectifs de Sécurité Risk Manager) in this step. This method was developed by the ANSSI (French National Agency for Information Systems Security) and allows to determine security measures adapted to the threats and to put
Do
During this phase, it is necessary to implement the solutions established in the previous point. It also puts in place the development and application of specific procedures as well as the awareness and training of your employees.
Check
In this stage, audits must be conducted to ensure that the solutions put in place to mitigate the risks are properly applied and effective. It is therefore in this stage that we will ensure compliance with security requirements.
Act
Finally, the Act or React step will allow you to correct the defects that could remain after the Do step. It will allow us to adjust some points, to improve them or to carry out preventive actions.
Then it's just a matter of repeating these steps as part of the continuous improvement process.
The SOC 2 based on the Trust Service Criteria
SOC 2 is not based on the 4 principles of DICT like ISO 27001, but on 5 criteria called Trust Service Criteria (TSC). These 5 criteria are security, availability, processing integrity, confidentiality and privacy.
Availability, integrity and confidentiality are concepts already defined and used within ISO 27001, nevertheless traceability is replaced in SOC2 in favor of security and privacy.
Security
It is the protection of information and systems against unauthorized access. Here, firewalls, two-factor identification, etc. can be used.
Privacy
In this part, the SOC 2 report will verify that a company is able to protect its personal data. These data are all the data that will allow us to identify a person (names, first names, addresses, health information...).
The SOC 2 reports will therefore specify whether a company is able to respect its 5 principles.
Why would you want to pass ISO 27001 or SOC 2
Both ISO 27001 and SOC 2 will be awarded to you after an audit and if you have validated the criteria. These are not mandatory for companies but they remain very interesting. Indeed, the fact of attesting that you have an effective and robust IT security policy will allow you to work with more customers. Having the ISO 27001 certification or a SOC report attesting that you meet the requirements defined in it will give a more reassuring image of your company. It is therefore in your company's best interest to be certified, as it is an advantage both for your security and for your expansion in the market.
The ISO 27001 and SOC 2 of the major actors of cybersecurity
ISO 27001 and SOC 2 are therefore very important actors in cybersecurity. They allow both to secure your infrastructure and your data and to improve your image with your customers and potential customers. They can also be a good way to start complying with the GDPR (General Data Protection Regulation). Securing your data is the main goal of the GDPR. Indeed, all actors using personal data must comply with this European regulation (if they operate or are located in Europe). Therefore, the challenge for a large number of companies is to know if they will be able to manage personal data. To start, passing an ISO27001 certification or a SOC 2 audit would be a good starting point. At Cryptr we care about your security and the security of your information.
Ready to learn more? We'll tell you more at Cryptr. Feel free to follow our latest news on Twitter and LinkedIn.
Add enterprise SSO for free
Cryptr simplifies user management for your business: quick setup, guaranteed security, and multiple free features. With robust authentication and easy, fast configuration, we meet businesses' security needs hassle-free.