The advantages of SSO authentication for your SaaS
by Malo Jamain, Business Developer
For several years, the world of work has experienced the advent of the SaaS (Software as a Service) model, with the pandemic and teleworking further accelerating the adoption of new online applications.
The number of SaaS used has never been greater, often reaching several hundred within large groups.
As a BetterCloud report from 2021 illustrates, companies with more than 10,000 employees use an average of 447 different SaaS solutions.
Most of a company's departments (marketing, finance, HR, accounting, etc.) are now users of SaaS solutions.
The moderate cost of these solutions and their ease of implementation have favored the decentralization of decision-making circuits for the acquisition of these tools outside the IT department, and enabled the business teams to be autonomous in their deployments.
The solutions offered are varied, ranging from project management with solutions like Trello, customer relationship management with solutions like HubSpot or Salesforce, to invoicing or design with solutions like Stripe or even Figma.
An essential point remains in the phase of setting up and deploying SaaS solutions in large companies: the compliance of SaaS in terms of security requirements, particularly on the authentication part with the SSO connection.
Used for years within large groups, Single Sign On (SSO) authentication allows an employee to simply access multiple applications with a single identifier from anywhere and with any device, while remaining at the highest level of security.
How does SSO authentication work?
Single Sign On authentication is an authentication process that allows users to securely access multiple applications using a single set of username and password.
Once the SSO authentication is in place, employees of a company will be able to access all the applications and all the websites available within their company by registering only once.
In other words, SSO authentication allows access to multiple systems by connecting to a single system, rather than multiplying usernames and passwords across all applications.
This authentication process is made possible thanks to the relationship of trust established between two entities: the identity provider (IdP) which is a digital identity manager (solutions such as Okta or Ping Identity), and the application to which a user wishes to access, the service provider (SP).
Communication between these two entities takes place via an IT standard allowing the exchange of security-related information: SAML (Security Assertion Markup Language) assertions.
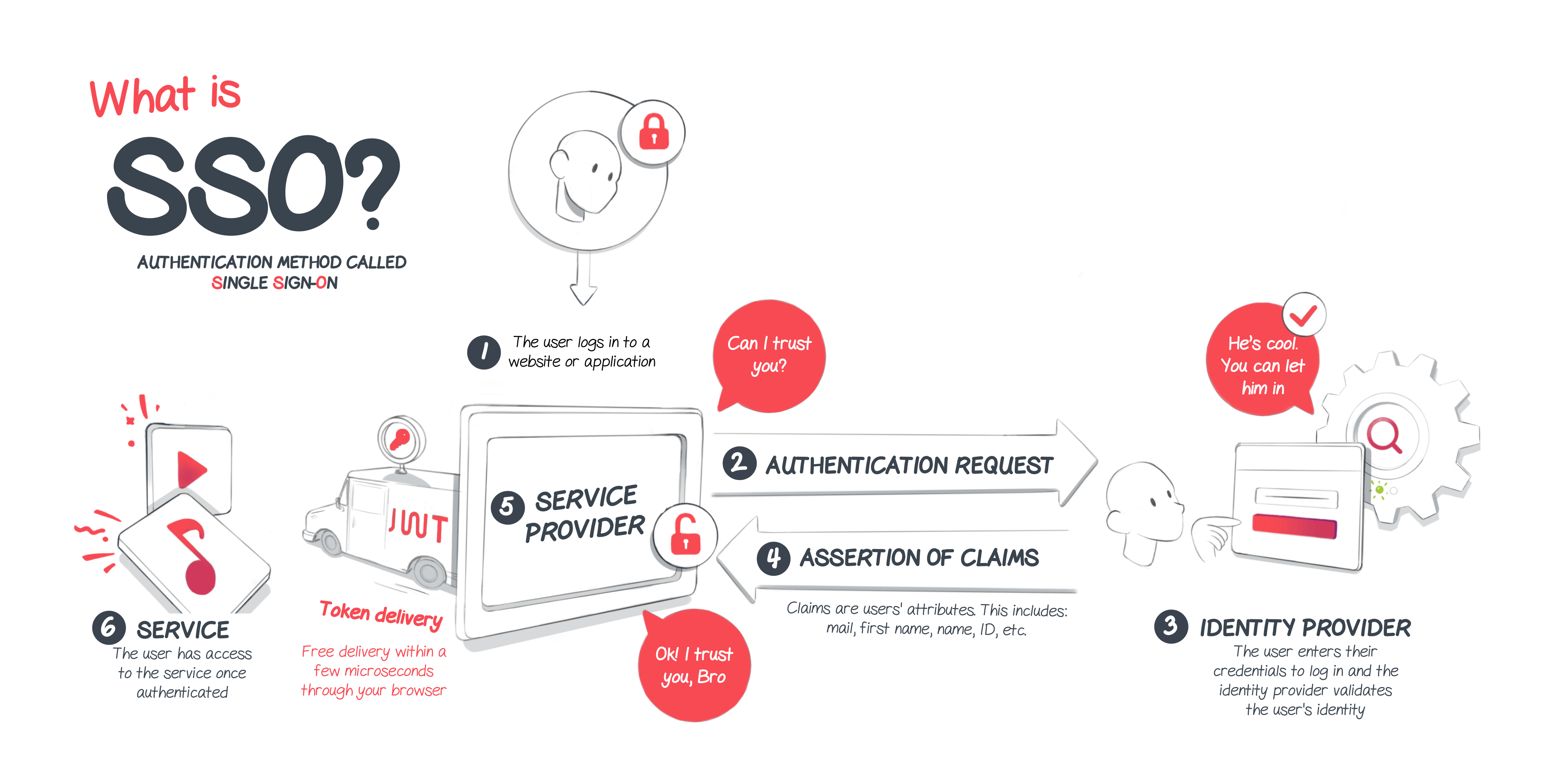
If the user is not authenticated, here are the different steps of the SSO connection:
-
The user accesses the service provider (SP) from the internet or the application
-
The service provider sends a request to the identity provider
-
The user is asked to enter the identifiers of the identity provider (username + password)
-
The identity provider validates the identifiers (or not) and in turn sends a SAML assertion to the service provider attesting to the validity of the authentication
-
The service provider authorizes the connection of the user
-
The user can enjoy the service he wanted to access
What are the benefits of SSO login?
An increased productivity
Within companies, employees access a large number of cloud applications on a daily basis to do their jobs.
Thanks to Single Sign On authentication, the time spent by employees logging in and managing their password is considerably reduced, which greatly facilitates their daily activities.
Users only need to remember one password rather than dozens.
Some identity providers also have an autofill feature for the password field, which completely eliminates the need to remember your password.
In addition, SSO authentication providers provide access to a platform in which the employee can find all the applications he can access to do his job.
The time spent remembering passwords and resetting them is therefore reduced to zero.
A greater security
SSO drastically reduces the risk of account hacking.
Indeed, with this authentication method, users no longer have different passwords across the applications they use, but a single password allowing them to access all applications.
Since users only have one password to remember, it is much easier to create a much more complex and robust password or phrase password.
SSO also reduces the repetition of passwords across applications, and eliminates the need to write down passwords on a piece of paper to remember them.
In addition, Single Sign On reduces account sharing. Indeed, a collaborator could share his password on an application with a colleague in order to help him, but if this password gives access to all the applications, then it is likely that the collaborator does not share his password. outmoded.
In order to have maximum security during authentication, it may be wise to combine SSO with another authentication factor, and thus to set up multi-factor authentication.
Reduced IT maintenance costs
The more different passwords a user has, the greater the risk of forgetting, and the higher the costs for the support team.
According to a recent study by Gartner, the cost of managing passwords is $70 to $200 per user.
If the user has a unique password, the chances of them calling on your customer support are therefore lower, and the time spent by your support teams solving problems related to passwords is reduced.
A better user experience
Regardless of your field of activity, whether you are a marketplace type website or a SaaS, too much complexity in authentication will have consequences on the shopping cart or the level of use of your solution.
The advantage of SSO is to quickly integrate your application into your users' daily lives, rather than confusing them with the creation of a new account in an external application.
Being able to log in to your application with the credentials they use on a daily basis reduces friction and makes the experience smoother for your users.
An application where the authentication process is laborious will frustrate users, and will not have as high a usage rate as an application offering a simpler experience.
Thanks to SSO, you put all the chances on your side to promote the adoption and use of your application.
Regulatory compliance
Several regulations concerning data protection, in particular the Sarbanes-Oxley regulation, the HIPAA regulation or the GDPR, impose rules on companies in order to protect data against cyber criminals.
In addition, the PCI DSS (Payment Card Industry Data Security Standard) regulations require companies to assign a unique identifier to all employees to allow them to access the various company resources.
In the event of a breach, the consequences can be serious for companies (fines, loss of customer confidence, etc.).
Implementing SSO early in its product lifecycle means complying with the regulations in force from the start and ensuring the secure sharing of company resources.
Being connected to the SSO system allows SaaS solutions to be visible as a full partner to the IT department, which can thus have a more complete visibility of the solutions used by the company.
Thus the SaaS connected in SSO can be part of a long-term relationship with its client.
A quick implementation with Cryptr
At Cryptr we want to provide the most enjoyable experience possible for developers, so that you can offer the authentication that best suits the needs of your customers.
Thanks to our SSO API guide, it only takes a few hours to enable the SSO connection on your SaaS.
Our successful developer team is there to support you in setting up the solution and allow you to offer your customers SSO authentication as quickly as possible, and regardless of the identity provider used by your customers (Azure AD, Google, Okta, Ping Identity, SiteMinder, IBM Security Verify, etc.).
If you are thinking of integrating SSO authentication on your SaaS, it is possible to access a test version of Cryptr, in order to allow you to test the SSO connection in a sandbox environment, and with the identity provider of your choice.
Once Cryptr is implemented, onboarding new customers in SSO becomes child's play.
All you have to do is send a URL link to your client's IT Admin, who is then autonomous in configuring his SSO system on your SaaS, thanks to our self-service onboarding:

Once the person in charge of IT at your client clicks on the URL, they access an interactive step-by-step onboarding, guiding them from A to Z in setting up the SSO connection on your SaaS.
Once the identity provider has been selected, a step-by-step onboarding is guiding your customer thanks to screenshots indicating where to retrieve the various information (ACS URL, SLO, X509 certificate etc.)
The average time to complete this step-by-step onboarding is 5 minutes, and this allows your technical teams to focus on other topics rather than having meetings with your customers to exchange this different information.
In summary, the SSO connection allows you to have reinforced security, a more pleasant experience for your users, and less time spent by your support teams managing password-related issues.
SSO login is even more attractive when combined with a directory synchronization strategy with your customers.
Cryptr's Directory Sync allows you to have a permanently up-to-date user directory with the user database present at your client: the attributes of your users are permanently up-to-date, and there is no longer any need to manually provision users.
For more information on our various authentication products, do not hesitate to follow us on LinkedIn, Twitter, YouTube and Instagram.
And to talk with our teams about the SSO connection on your SaaS, you can book the slot of your choice here: Meet Cryptr
Add enterprise SSO for free
Cryptr simplifies user management for your business: quick setup, guaranteed security, and multiple free features. With robust authentication and easy, fast configuration, we meet businesses' security needs hassle-free.